How to Fix TLSv1 Alert Protocol Version

A new client came to me with an interesting problem. She was able to access her WordPress site on phone and Kindle but not on either one of her laptops.
When she tried to use either laptop, she’d get the following error with both Chrome and Firefox browsers:
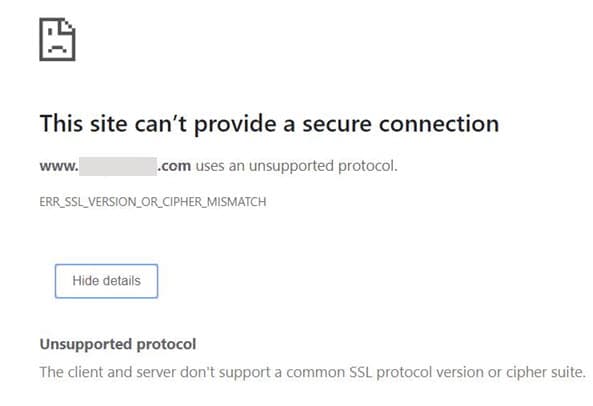
This screenshot meant that some browsers were unable to negotiate a protocol for connection.
Now this site was running with a valid SSL certificate. And I had no problems accessing her site on desktop.
But I couldn’t load her site on my Android phone or tablet. And she couldn’t load her site on either of her laptops.
Troubleshoot TLSv1 Alert Protocol Version
Was Antivirus Software the Problem?
Unsure as to how to troubleshoot the issue, I did some research on Google and found a few blog posts that mentioned the issue could be due to a conflict with antivirus software.
So I started down the path of checking antivirus settings on both my phone and tablet.
I use McAfee and it has a Safe Wi-Fi setting. When I turned it off, the site loaded just fine.
I then asked my client to check into her Kapersky antivirus settings.
She discovered that if she enabled “Scan encrypted connections upon request from protection components” her site would then load on her laptop.
It just didn’t make sense that a user would have to adjust settings on their devices in order for their website to load.
And that would mean anybody using the same devices would be unable to access the website.
So there had to be something at a higher level in the configuration of the site that was causing the problem.
That’s when I began running diagnostics to troubleshoot.
TLSv1 Alert Protocol Version Error
While running header checks on WebSitePulse, I received the following alert:
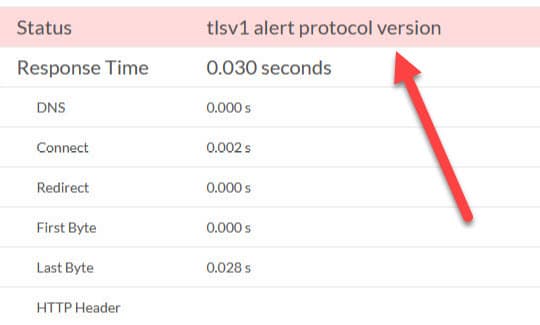
Now we were getting somewhere! But what did that TLSv1 Alert Protocol Version error mean?
I searched throughout the internet again and could get no clear answer to why that error was appearing or what to do about it.
I finally contacted the client’s web hosting company to see if it was a server configuration issue.
And that’s when we started to get clarity.
Was Cloudflare the Problem?
This particular website was configured to run through Cloudflare.
So after running some additional tests on Qualys SSL Labs, we realized the issue was with the TLS version.
The only supported TLS version for this website was Version 1.3, which is the latest version as of August 2018.
TLS Defined
Without getting too technical, TLS refers to Transport Layer Security, which has replaced Secure Sockets Layer (SSL).
TLS strives to provide security and data integrity between users and servers through encryption and authentication. You can learn more about TLS here.
When web traffic is encrypted with TLS, users will see the green padlock in their browser window.
Although TLS 1.3 is the most modern protocol, other existing protocols such as TLS 1, 1.1, and 1.2 are still in place to support older browsers.
And if those protocols are not enabled on a given website, visitors using older browsers will not be able to load the site.
For additional information, you can check this table to see which browsers currently support TLS 1.3.
How to Fix TLSv1 Alert Protocol Version
So the root problem on this site’s configuration was at Cloudflare, where the TLS version was set to 1.3.
This setting cut off a large amount of visitors using older browsers and they couldn’t access the website.
The hosting company recommended that we set the minimum version to TLS 1.2, which is supported by most clients (browsers).
That setting can be found at Cloudflare under SSL/TLS > Edge Certificates:
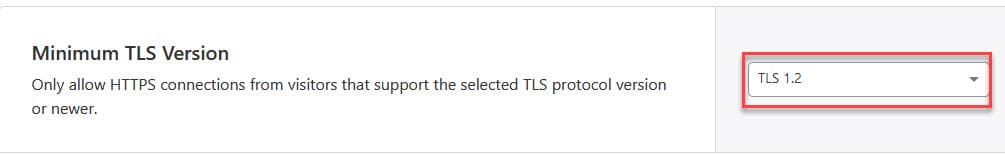
Click the dropdown and set it to TLS 1.2.
Enable TLS 1.3 and 0-RTT Speed Boost for Previous Clients
We were also advised that we could enable TLS 1.3 and 0-RTT under the TLS 1.3 setting on Cloudflare.
0-RTT ( zero round trip time resumption ) is a feature that boosts performance for clients who have previously connected to your website.
If you scroll down just a bit, you can also enable the TLS 1.3 protocol when supported by browsers. And you can enable 0-RTT at the same time.
Apache or Nginx
If your site runs on either Apache or Nginx, check the server configuration file to ensure that newer TLS versions are supported.
While correcting this issue will resolve the TSLv1 alert protocol error, it does not guarantee that your website security is not compromised.
Ongoing testing and security audits are important to the health of your website.
Over to You
While it’s important to stay on top of the latest technologies, you do need to be mindful of not jumping on the latest protocol too quickly as you can cut off a large chunk of your visitors.
And it’s super important to make sure that WordPress websites are properly secured from the ground up.
That’s why I continue to encourage WordPress web designers to take this in-depth webmaster training and stay ahead of the curve.
It took some time to isolate and fix TLSv1 Alert Protocol Version error but it was a worthwhile learning experience and knowledge that will help the next time around.